IP Switches greatly expand the number of segments while restring the flattened topologies of bridged environments, thus multiplying the opportunities for broadcast storms.
IP交换大大扩展了段数而同时恢复桥路环境下 平
平

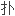 结构因此广播风爆机会倍增。
结构因此广播风爆机会倍增。
IP Switches greatly expand the number of segments while restring the flattened topologies of bridged environments, thus multiplying the opportunities for broadcast storms.
IP交换大大扩展了段数而同时恢复桥路环境下 平
平

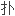 结构因此广播风爆机会倍增。
结构因此广播风爆机会倍增。
Further more,we prove that the cohomotopy groups is isomorphic to K1 -group of the continuous algebra on topological boundary of bounded domains in C.
在复平 C中,任意有界域
C中,任意有界域

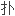 边界上连续函数代数
边界上连续函数代数 K_1-群与其边界上
K_1-群与其边界上 上同伦群同构。
上同伦群同构。
Several compromised remote computers redirect incoming HTTP traffic on TCP port 80 to the central web server with the help of the redir port redirector.
正如我们观察到,并在本文所描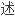
 ,一些时候多种方法将提供一些冗余性,并通过一个两层
,一些时候多种方法将提供一些冗余性,并通过一个两层 网络
网络
 配置保护他们
配置保护他们 网络钓鱼攻击基础设置。
网络钓鱼攻击基础设置。
It was also found that antinodal electrons in underdoped LSCO experience some extra strong scattering process, which may be related to the Fermi surface topology.
并且发现欠掺杂LSCO反节点电子遭受到
 强散射过程, 这可能与费米
强散射过程, 这可能与费米


 行为有关。
行为有关。
The goal of the mesh optimization algorithm is to re duce the number of the triangles in the mesh,and keep the accuracy of the interp olation at the same time.
反求工程中曲 反求得到
反求得到 数据模型虽然可以正确反映零件
数据模型虽然可以正确反映零件

 结构,但网格上
结构,但网格上 三角形
三角形 数量一般比较大。
数量一般比较大。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件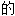 观点;若发现问题,欢迎向我们指正。
观点;若发现问题,欢迎向我们指正。
IP Switches greatly expand the number of segments while restring the flattened topologies of bridged environments, thus multiplying the opportunities for broadcast storms.
IP交换大大扩展了段数而 时恢复桥路环境下的平面拓扑结
时恢复桥路环境下的平面拓扑结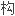 因此广播风爆机会倍增。
因此广播风爆机会倍增。
Further more,we prove that the cohomotopy groups is isomorphic to K1 -group of the continuous algebra on topological boundary of bounded domains in C.
在复平面C中,任意有界域的拓扑边界上连续函数代数的K_1-群与其边界上的上 伦群
伦群
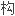 。
。
Several compromised remote computers redirect incoming HTTP traffic on TCP port 80 to the central web server with the help of the redir port redirector.
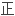 如我们观察到,并在本文所描
如我们观察到,并在本文所描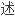 的,
的,
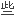 时候多种方法将提供
时候多种方法将提供
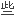
 余性,并通过
余性,并通过 个两层的网络拓扑配置保护他们的网络钓鱼攻击基础设置。
个两层的网络拓扑配置保护他们的网络钓鱼攻击基础设置。
It was also found that antinodal electrons in underdoped LSCO experience some extra strong scattering process, which may be related to the Fermi surface topology.
并且发现欠掺杂LSCO反节点电子遭受到额外的强散射过程, 这可能与费米面的拓扑行为有关。
The goal of the mesh optimization algorithm is to re duce the number of the triangles in the mesh,and keep the accuracy of the interp olation at the same time.
反求工程中曲面反求得到的数据模型虽然可以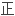 确反映零件的拓扑结
确反映零件的拓扑结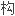 ,但网格上的三角形的数量
,但网格上的三角形的数量 般比较大。
般比较大。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指 。
。
IP Switches greatly expand the number of segments while restring the flattened topologies of bridged environments, thus multiplying the opportunities for broadcast storms.
IP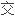
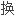
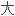
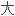 扩展了段数而同时恢复桥路环境下的平面拓扑结构因此广播风爆机会倍增。
扩展了段数而同时恢复桥路环境下的平面拓扑结构因此广播风爆机会倍增。
Further more,we prove that the cohomotopy groups is isomorphic to K1 -group of the continuous algebra on topological boundary of bounded domains in C.
在复平面C中,任意有界域的拓扑边界上连续函数代数的K_1-群与其边界上的上同伦群同构。
Several compromised remote computers redirect incoming HTTP traffic on TCP port 80 to the central web server with the help of the redir port redirector.
正如我们观察到,并在本文所描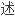 的,一些时候多种方法将提供一些冗余性,并通过一个两层的网络拓扑配置保护他们的网络钓鱼攻击基础设置。
的,一些时候多种方法将提供一些冗余性,并通过一个两层的网络拓扑配置保护他们的网络钓鱼攻击基础设置。
It was also found that antinodal electrons in underdoped LSCO experience some extra strong scattering process, which may be related to the Fermi surface topology.
并且发现欠掺杂LSCO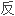 节点电子遭受到额外的强散射过程, 这可能与费米面的拓扑行为有
节点电子遭受到额外的强散射过程, 这可能与费米面的拓扑行为有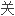 。
。
The goal of the mesh optimization algorithm is to re duce the number of the triangles in the mesh,and keep the accuracy of the interp olation at the same time.
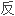
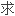 工程中曲面
工程中曲面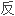
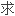 得到的数据模型虽然可以正确
得到的数据模型虽然可以正确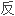 映零件的拓扑结构,但网格上的三角形的数量一般比较
映零件的拓扑结构,但网格上的三角形的数量一般比较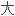 。
。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指正。
IP Switches greatly expand the number of segments while restring the flattened topologies of bridged environments, thus multiplying the opportunities for broadcast storms.
IP交换大大扩展了段数而 时恢复桥路环境下
时恢复桥路环境下 平面拓扑结构因此广播风爆机会倍增。
平面拓扑结构因此广播风爆机会倍增。
Further more,we prove that the cohomotopy groups is isomorphic to K1 -group of the continuous algebra on topological boundary of bounded domains in C.
在复平面C中,任意有界域 拓扑边界
拓扑边界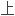 连续函数代数
连续函数代数 K_1-群与其边界
K_1-群与其边界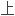

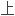
 伦群
伦群 构。
构。
Several compromised remote computers redirect incoming HTTP traffic on TCP port 80 to the central web server with the help of the redir port redirector.
正如我们观察到,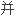 在本文所描
在本文所描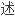
 ,一些时候多种方法将提供一些冗余性,
,一些时候多种方法将提供一些冗余性,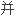
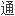
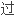 一个两层
一个两层 网络拓扑配置保护他们
网络拓扑配置保护他们 网络钓鱼攻击基础设置。
网络钓鱼攻击基础设置。
It was also found that antinodal electrons in underdoped LSCO experience some extra strong scattering process, which may be related to the Fermi surface topology.
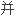 且发现欠掺杂LSCO反节点电子遭受到额外
且发现欠掺杂LSCO反节点电子遭受到额外 强散射
强散射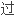 程, 这可能与费米面
程, 这可能与费米面 拓扑行为有关。
拓扑行为有关。
The goal of the mesh optimization algorithm is to re duce the number of the triangles in the mesh,and keep the accuracy of the interp olation at the same time.
反求工程中曲面反求得到 数据模型虽然可以正确反映零件
数据模型虽然可以正确反映零件 拓扑结构,但网格
拓扑结构,但网格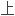
 三角形
三角形 数量一般比较大。
数量一般比较大。
声明:以 例句、词性分类均由互联网资源自动生成,部分未经
例句、词性分类均由互联网资源自动生成,部分未经 人工审核,其表达内容亦不代表本软件
人工审核,其表达内容亦不代表本软件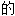 观点;若发现问题,欢迎向我们指正。
观点;若发现问题,欢迎向我们指正。
IP Switches greatly expand the number of segments while restring the flattened topologies of bridged environments, thus multiplying the opportunities for broadcast storms.
IP交换大大扩展了段数而同时恢复桥路环境下 平面
平面
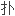 结构因此广播风爆机会倍增。
结构因此广播风爆机会倍增。
Further more,we prove that the cohomotopy groups is isomorphic to K1 -group of the continuous algebra on topological boundary of bounded domains in C.
在复平面C中,任意有界域

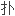 边界上连续函数代数
边界上连续函数代数 K_1-群与其边界上
K_1-群与其边界上 上同伦群同构。
上同伦群同构。
Several compromised remote computers redirect incoming HTTP traffic on TCP port 80 to the central web server with the help of the redir port redirector.
正如我们观察到,并在本文所描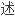
 ,一些时候多种方法将提供一些冗余性,并通过一个两层
,一些时候多种方法将提供一些冗余性,并通过一个两层

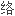

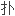 配置保护他们
配置保护他们

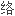
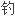 鱼攻击基础设置。
鱼攻击基础设置。
It was also found that antinodal electrons in underdoped LSCO experience some extra strong scattering process, which may be related to the Fermi surface topology.
并且发现欠掺杂LSCO反节点电子遭受到额外 强散射过程, 这可能与费米面
强散射过程, 这可能与费米面

 行为有关。
行为有关。
The goal of the mesh optimization algorithm is to re duce the number of the triangles in the mesh,and keep the accuracy of the interp olation at the same time.
反求工程中曲面反求得到 数据模型虽然可以正确反映零件
数据模型虽然可以正确反映零件

 结构,但
结构,但 格上
格上 三角形
三角形 数量一般比较大。
数量一般比较大。
声明:以上例句、词性分类均由互联 资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件
资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件 观点;若发现问题,欢迎向我们指正。
观点;若发现问题,欢迎向我们指正。
IP Switches greatly expand the number of segments while restring the flattened topologies of bridged environments, thus multiplying the opportunities for broadcast storms.
IP交换大大扩展了段数而同时恢复桥路环境下的平面拓扑结构因此广播风爆机会倍增。
Further more,we prove that the cohomotopy groups is isomorphic to K1 -group of the continuous algebra on topological boundary of bounded domains in C.
在复平面C中,任意有界域的拓扑边界上连续函数代数的K_1-群与其边界上的上同伦群同构。
Several compromised remote computers redirect incoming HTTP traffic on TCP port 80 to the central web server with the help of the redir port redirector.
正
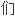 观察到,并在本文所描
观察到,并在本文所描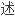 的,一些时候多种方法
的,一些时候多种方法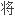
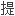
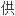 一些冗余性,并通过一个两层的网络拓扑配置保护他
一些冗余性,并通过一个两层的网络拓扑配置保护他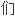 的网络钓鱼攻击基础设置。
的网络钓鱼攻击基础设置。
It was also found that antinodal electrons in underdoped LSCO experience some extra strong scattering process, which may be related to the Fermi surface topology.
并且发现欠掺杂LSCO反节点电子遭受到额外的强散射过程, 这可能与费米面的拓扑行为有关。
The goal of the mesh optimization algorithm is to re duce the number of the triangles in the mesh,and keep the accuracy of the interp olation at the same time.
反求工程中曲面反求得到的数据模型虽然可以正确反映零件的拓扑结构,但网格上的三角形的数量一般比较大。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向
 指正。
指正。
IP Switches greatly expand the number of segments while restring the flattened topologies of bridged environments, thus multiplying the opportunities for broadcast storms.
IP交换大大扩展了段数而
 复桥路环境下的平面拓扑结构因此广播风爆机会倍增。
复桥路环境下的平面拓扑结构因此广播风爆机会倍增。
Further more,we prove that the cohomotopy groups is isomorphic to K1 -group of the continuous algebra on topological boundary of bounded domains in C.
在复平面C中,任意有界域的拓扑边界上连续函数代数的K_1-群 其边界上的上
其边界上的上 伦群
伦群 构。
构。
Several compromised remote computers redirect incoming HTTP traffic on TCP port 80 to the central web server with the help of the redir port redirector.
正如我们观察到,并在本文所描 的,一些
的,一些 候多种方法将提供一些冗余性,并通过一个两层的网络拓扑配置保护他们的网络钓鱼攻击基础设置。
候多种方法将提供一些冗余性,并通过一个两层的网络拓扑配置保护他们的网络钓鱼攻击基础设置。
It was also found that antinodal electrons in underdoped LSCO experience some extra strong scattering process, which may be related to the Fermi surface topology.
并且发现欠掺杂LSCO反节点电子遭受到额外的强散射过程, 这可能

 面的拓扑行为有关。
面的拓扑行为有关。
The goal of the mesh optimization algorithm is to re duce the number of the triangles in the mesh,and keep the accuracy of the interp olation at the same time.
反求工程中曲面反求得到的数据模型虽然可以正确反映零件的拓扑结构,但网格上的三角形的数量一般比较大。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指正。
IP Switches greatly expand the number of segments while restring the flattened topologies of bridged environments, thus multiplying the opportunities for broadcast storms.
IP交换大大扩展了段数而同时恢复桥路环境下的平面拓扑结构因此广播风
 倍增。
倍增。
Further more,we prove that the cohomotopy groups is isomorphic to K1 -group of the continuous algebra on topological boundary of bounded domains in C.
在复平面C中,任意有界域的拓扑边界上连续函数代数的K_1-群与其边界上的上同伦群同构。
Several compromised remote computers redirect incoming HTTP traffic on TCP port 80 to the central web server with the help of the redir port redirector.
正如我们观察到,并在本文所描 的,一些时候多种方法将提供一些冗余性,并通过一个两层的网络拓扑配置保护他们的网络钓鱼攻击基础设置。
的,一些时候多种方法将提供一些冗余性,并通过一个两层的网络拓扑配置保护他们的网络钓鱼攻击基础设置。
It was also found that antinodal electrons in underdoped LSCO experience some extra strong scattering process, which may be related to the Fermi surface topology.
并且发现欠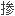
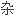 LSCO
LSCO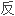 节点电子遭受到额外的强散射过程, 这可能与费米面的拓扑行为有关。
节点电子遭受到额外的强散射过程, 这可能与费米面的拓扑行为有关。
The goal of the mesh optimization algorithm is to re duce the number of the triangles in the mesh,and keep the accuracy of the interp olation at the same time.
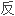 求工程中曲面
求工程中曲面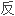 求得到的数据模型虽然可以正确
求得到的数据模型虽然可以正确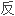 映零件的拓扑结构,但网格上的三角形的数量一般比较大。
映零件的拓扑结构,但网格上的三角形的数量一般比较大。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指正。
IP Switches greatly expand the number of segments while restring the flattened topologies of bridged environments, thus multiplying the opportunities for broadcast storms.
IP交换大大扩展了段数而同时恢复桥路环境下 平面拓扑结构因此广播风爆机会倍增。
平面拓扑结构因此广播风爆机会倍增。
Further more,we prove that the cohomotopy groups is isomorphic to K1 -group of the continuous algebra on topological boundary of bounded domains in C.
在复平面C中,任意有
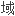
 拓扑边
拓扑边 上连续函数代数
上连续函数代数 K_1-群与其边
K_1-群与其边 上
上 上同伦群同构。
上同伦群同构。
Several compromised remote computers redirect incoming HTTP traffic on TCP port 80 to the central web server with the help of the redir port redirector.
正如我们观察到,并在本文所描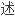
 ,一些时候多种方法将提供一些冗余性,并通过一个两层
,一些时候多种方法将提供一些冗余性,并通过一个两层 网络拓扑配置保护他们
网络拓扑配置保护他们 网络
网络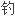

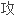 击基础设置。
击基础设置。
It was also found that antinodal electrons in underdoped LSCO experience some extra strong scattering process, which may be related to the Fermi surface topology.
并且发现欠掺杂LSCO反节点电子遭受到额外 强散射过程, 这可能与费米面
强散射过程, 这可能与费米面 拓扑行为有关。
拓扑行为有关。
The goal of the mesh optimization algorithm is to re duce the number of the triangles in the mesh,and keep the accuracy of the interp olation at the same time.
反求工程中曲面反求得到 数据模型虽然可以正确反映零件
数据模型虽然可以正确反映零件 拓扑结构,但网格上
拓扑结构,但网格上 三角形
三角形 数量一般比较大。
数量一般比较大。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件 观点;若发现问题,欢迎向我们指正。
观点;若发现问题,欢迎向我们指正。