Hadorwould traditionary symmetry encryption and publicity secret key mode band together, have two both the virtue.
将传统的对称性加 与公开
与公开
 方法
方法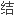

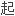 来,兼备了两者的优点。
来,兼备了两者的优点。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指正。
 济学人 Science and technology
济学人 Science and technology  济学人 Science and technology
济学人 Science and technology